firewall log search tool (Thoughtful) Holidays Gift Ideas for Less Than $15 + 1 Bonus Idea

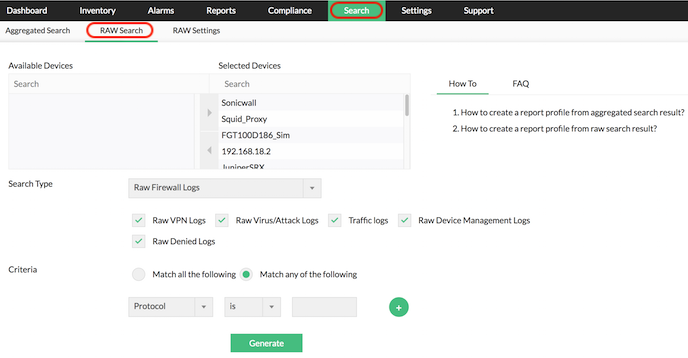
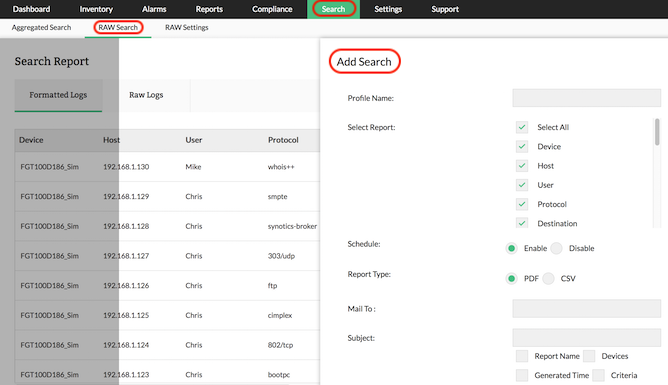
Firewall Raw Log Search and Reports :: Firewall Analyzer
Firewall Analyzer is a firewall log analysis tool that collects, analyses and reports information on enterprise-wide firewalls, proxy servers, and VPNs. It provides .
http://www.manageengine.com/products/firewall/firewall-rawlog-search-reports.html
Firewall Log Analysis & Reporting Software :: Firewall Analyzer ...
Firewall Analyzer is a web-based firewall, VPN, and proxy server log analysis . Security tools like Firewalls, VPN, and Proxy Servers generate a huge quantity of . Raw Log search; Unused Firewall Rules Report; On-Demand and Real-time .
http://www.manageengine.com/products/firewall/firewall-analyzer-product-brochure.html
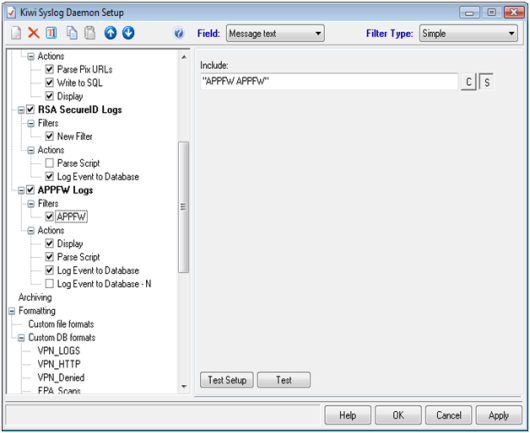
LogAnalyzer Basics
Probably more interesting, you can invoke the cross-datasource search tool and obtain information on what the firewall log has recorded about the IPs in .
http://loganalyzer.adiscon.com/doc/basics.html

| Framed Photos or Artwork |
Learn How to Use PowerShell to Parse the Firewall Log - Hey ...
Aug 3, 2011 . I am wondering about the firewall log on my computer. . Oh, yeah, if there is a firewall log, can you show me how to use Windows PowerShell to search it for . The NetSh utility can be used to obtain logging locations for the .
http://blogs.technet.com/b/heyscriptingguy/archive/2011/08/03/learn-how-to-use-powershell-to-parse-the-firewall-log.aspx
Firewall Log Analysis
Sep 3, 2008 . Posted in Firewall log analysis | Leave a Comment » . website is getting indexed in all these search engines, increasing the visitors to the site.
http://firegen.wordpress.com/
Using Firewall Log to Solve upnp Problem
If so where is firewall log written. I have turned on logging but cannot find log. Also how can I read it. There used to be a log viewing tool in Yast .
http://forums.opensuse.org/english/get-technical-help-here/network-internet/472234-using-firewall-log-solve-upnp-problem.html
How to interpret MAC from iptables firewall log
. MAC address from next line take it from /var/log/messages ACCEPT:IN=eth0 OUT= . Download kernel source from kernel.org or install it using your distros command line tool. . Search Engine Optimization by vBSEO 3.6.0 .
http://nixcraft.com/linux-software/16580-how-interpret-mac-iptables-firewall-log.html
SonicWall Firewall Log Messages - Firewall - General-Networking
Recently installed a SonicWall TZ170 firewall in my home network environment. Set up the . You have searched for "SonicWall Firewall Log Messages" . You might be . Is this possibly a file sharing program that one of my .
http://www.tomshardware.com/forum/13026-42-sonicwall-firewall-messages
Firewall security log analyzers
Products 1 - 8 of 8 . Firewall security log analyzers. Back to category listing .
http://www.windowsecurity.com/software/Firewall-security-log-analyzers/
Firewall Logs - PFSenseDocs
Nov 17, 2009 . Personal tools. Log in . Jump to: navigation, search. The Firewall logs at Status > System Logs on the Firewall tab show all of the logged .
http://doc.pfsense.org/index.php/Firewall_Logs
| Oeno Writers With Bottle of Wine |
PC Tools Firewall Log File | 27 of 30
Double-clicking a log entry within the PC Tools Firewall Plus 2.0 log reveals more information about the . Spybot Search & Destroy: The Right Tool for the Job?
http://www.techrepublic.com/photos/pc-tools-firewall-plus-20-the-right-tool-for-the-job/64993?seq=27
show firewall log - Technical Documentation - Support - Juniper ...
Search Tips | New Search Engine . show firewall log <detail><interface interface -name><logical-system . Display log information about firewall filters.
http://www.juniper.net/techpubs/en_US/junos11.2/topics/reference/command-summary/show-firewall-log.html
Vyatta.org :: View topic - Wflogs firewall log analysis GUI tool
Wflogs is a firewall log analysis tool. It can be used to produce a log summary report in plain text, HTML and XML, or to monitor firewalling logs .
http://www.vyatta.org/forum/viewtopic.php?p=32375
Read your firewall logs! - ZDNet
Jul 5, 2001 . Companies; Hardware; Software; Mobile; Security; Research; Special Coverage . By reviewing your firewall logs, you can determine whether new IP addresses are . The new iPad is a good tool for getting things done.
http://www.zdnet.com/news/read-your-firewall-logs/298230
Manual:System/Log - MikroTik Wiki
Dec 9, 2010 . Jump to: navigation, search . RouterOS is capable of logging various system events and status information. . system,info,account user admin logged out from 10.1.101.212 via telnet 01:01:58 firewall,info input: in:ether1 out:(none), . ddns, Log messages generated by Manual:Tools/Dynamic DNS tool .
http://wiki.mikrotik.com/wiki/Manual:System/Log
| Personalized Travel or Restaurant Guide |
Traffic mining firewall logs could improve network security
Apr 16, 2010 . ScienceDaily: Your source for the latest research news and science . However, these static approaches ignore the Firewall log files which change . New Program Points Out Vulnerabilities, Calculates Risk Of Attack (July 23, .
http://www.sciencedaily.com/releases/2010/04/100416095758.htm
Firewall Logging using a Microsoft SQL database
Mar 11, 2008 . How to set up ISA Server 2006 firewall logging with a Microsoft SQL . Database Engine) to provide logging for the Microsoft Firewall- and .
http://www.isaserver.org/tutorials/Firewall-Logging-Microsoft-SQL-database.html
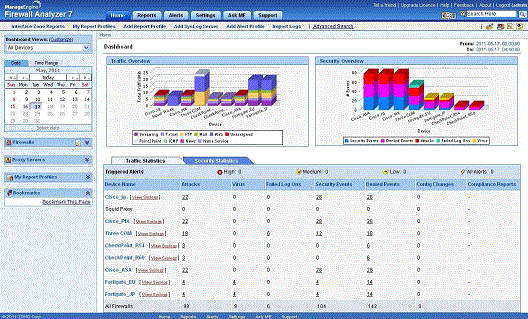
AdventNet Upgrades Firewall Analyzer With Comprehensive Raw Log
Apr 2, 2008. Log Search for Forensic Analysis and New Firewall Policies Usage . of Firewall Analyzer 5.0, the security and traffic monitoring tool with .
http://www.manageengine.com/news/upgrade-firewall.html
| Print or Internet Subscriptions |
Analyzing Firewall Logs > Cisco ASA and PIX Firewall Logging
Nov 4, 2005 . Cisco Systems. Account Sign In Cart View Cart. Cisco Press. Search . Firewall logs can be collected and analyzed to determine what types of . of logging information, you might want to invest in a firewall log analysis tool.
http://www.ciscopress.com/articles/article.asp?p=424447&seqNum=4
EventLog Analyzer | Event Log Monitoring and Management
""This tool is very useful. If you have only a few moments to have a look at your Firewall log, you can rapidly have an idea of what's happening to your network. . Scheduling Reports; Raw Log Search and Reports; Historical Trend Analysis .
http://www.manageengine.ca/firewall-analyzer.aspx
Firewall log file, how to make several different log files with ...
Firewall log file, how to make several different log files with IPTables? . After a google search, I found that the Linux Firewall uses IPTables, .
http://www.linuxquestions.org/questions/linux-newbie-8/firewall-log-file-how-to-make-several-different-log-files-with-iptables-686583/
Main Page - Firewall log messages
Nov 27, 2011 . Firewall Log Entry Code Wiki . Use the search box on the left side of the screen to lookup various codes used in . Personal tools. Log in .
http://logwiki.firegen.com/
Unknown IP addresses in my firewall logs (outgoing initiated web ...
logs with their canonical names, not just an IP address. Am I being too paranoid here? If not . can use to find posts by me in a search engine: .
http://www.velocityreviews.com/forums/t578353-unknown-ip-addresses-in-my-firewall-logs-outgoing-initiated-web-traffic.html
Step 5: Viewing the Firewall Log
Nov 2, 2007 . Windows Firewall with Advanced Security and IPsec . Step 2: Allowing Unsolicited Inbound Network Traffic for a Specific Program . can import your log file into Microsoft Excel to more easily search, sort, and filter the entries.
http://technet.microsoft.com/en-us/library/cc753781(v=ws.10).aspx
Firewall logs are in /var/log/{firewall,warn,messages} - clutter
I suspect this is an initial configuration bug. All firewall logs seem to be going to all three files. That causes a lot of clutter in the log files,
http://forums.opensuse.org/english/get-technical-help-here/network-internet/456671-firewall-logs-var-log-firewall-warn-messages-clutter.html

| Do It Yourself Gift Baskets |
How to Add Logging to the Plesk Firewall - rackAID
Mar 12, 2007 . Learn how to add logging to your Plesk firewall. . How to Add Logging to the Plesk Firewall. Call Sales: 877-435-2445. Log In. Search Search . interface for configuring the firewall, the tool does not configure firewall logging.
http://www.rackaid.com/resources/how-to-add-logging-to-the-plesk-firewall/
Toolbox: Tail
Aug 15, 2005 . Use the Win32 version of this popular UNIX tool to complement grep and . that's running Windows Firewall and want to search the firewall log .
http://www.windowsitpro.com/article/log-files/toolbox-tail
Design and implement of firewall-log-based online attack detection ...
The system is up to firewall-log's online analysis, between-log relevancy checking, and . An architecture of pattern-oriented distributed meta-search engine .
http://dl.acm.org/citation.cfm?id=1046320
Visualizing Firewall Log Data to Detect Security
For the research in this paper, the Cisco firewall family (FWSM, . The first step in visualizing firewall log data is to collect it, and the tool typically used to achieve .
http://www.giac.org/paper/gcia/1651/visualizing-firewall-log-data-detect-security/109883
Ubuntu Server Guide - Logs
Firewall logs are essential for recognizing attacks, troubleshooting your . firewall logs can be simplified by using a log analyzing tool such as fwanalog, . Related Searches firewall logs fwlogwatch logging rules server guide dport firewall .
http://linux.about.com/od/ubusrv_doc/a/ubusg18t05.htm
Firewall Log - Windows-XP-General-Discussion - Windows-XP
You have searched for "Firewall Log" . You might be . Bottom Search this thread . informative, telling you what program accesses the web and what ip address .
http://www.tomshardware.com/forum/21227-45-firewall
Automating Firewall Log Scanning | Linux Journal
Jul 1, 2001 . Both of them can be found on the Internet by using any search engine. . We then proceed to build up a logging firewall using ipchains. First we .
http://www.linuxjournal.com/article/4543
Searching By Country in Raw Firewall Logs
The question was posed one day regarding firewall logs: What is the traffic recorded . There is a neat utility called 'grepcidr' by Jem Berkes which accomplishes this . Once PART A is completed searches can be performed for individual IPs, .
http://www.sazizan.net/main/countrylogs/countrylogs.htm
firewall-logging-paper
Jul 26, 2011 . Example Usage of Firewall Log Analysis Tool . . features. 5. Ad hoc search: unlike general purpose log management tools, dedicated firewall .
http://www.docstoc.com/docs/87103451/firewall-logging-paper
| Bonus Idea: Make It Yourself |
Sygate Firewall Log Viewer Addon - Weborum Webmaster Forum
The SPF Log Viewer is a tool created by one of our Sygate enthusiasts, . options for log data, ISC port reports search, event pattern analysis, .
http://forum.weborum.com/index.php?showtopic=1617
Checkpoint Firewall Log Analyzer - Free Software Download
Analyzes log data for Search Engine referred users with separate data for each search term. Plots changes over time. Firewall- 1 Log Report Summarizer .
http://www.sharewareconnection.com/software.php?list=Checkpoint+Firewall+Log+Analyzer
Windows Web Tools, Log Analyzers Software - Y! Downloads
Firewall Analyzer is a Web-based firewall log analysis tool that collects, correlates . This log analysis software process hits, bandwidth, search keywords and .
http://downloads.yahoo.com/software/windows-web-tools-t1271
Outpost Firewall Guide - HTTP Log
The Allowed log will just show the initial HTTP request (like to Google when you visit the Google search engine), where as this plugin will show you all the .
http://www.outpostfirewall.com/guide/the_outpost_gui/plugins/http_log.htm
free cisco firewall log analysis download
APBackUp 2.1 is an easy to use automatic backup utility… . Firewall Analyzer is a web-based firewall log analysis tool that collects, . Spybot search destroy .
http://3d2f.com/tags/cisco/firewall/log/analysis/

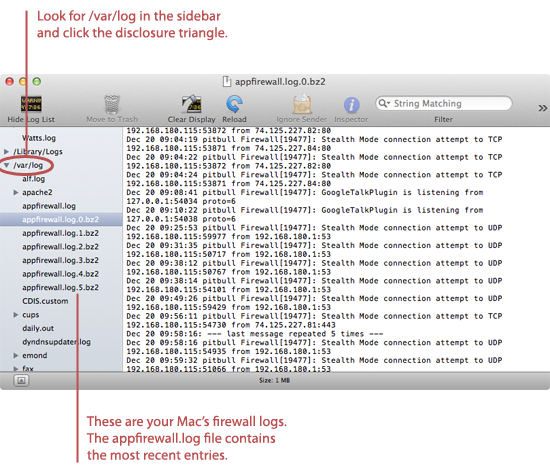

How To Review A Firewall Log In 15 Min Or Less – Part 2 ...
Sep 29, 2009 . In order to show you the process of white listing your firewall logs, I am going to use . Grep is a standard Linux/UNIX tool, with free versions available for . It allows you to search one or more files looking for a specific pattern.
http://www.chrisbrenton.org/2009/09/how-to-review-a-firewall-log-in-15-min-or-less-%E2%80%93-part-2/